Navigating SAP: GUI Scripting, User Roles, and Management Challenges
User Management: within SAP involves the creation, modification, and deletion of user accounts. This involves assigning user IDs, passwords, and authorizations to users based on their job roles and responsibilities. It is an imperative process for upholding the system’s security and integrity.
The users are recognized by the following data: mandatory data such as username and password, optional data such as full name or e-mail address, and user roles which decide the user’s authorizations.
If more than one role is assigned to a user, a synchronization process is activated to prevent overlapping of duties. This user management also allows you to add, edit, or delete users, restore the default search input and output fields for users who have configured their search options, as well as unlock users who are locked by the system after multiple failed logon attempts.
Role Management: In SAP, Role Management is the act of creating, changing, and eliminating roles. These roles are based on users’ job roles and responsibilities and serve to control user access to various features and data within the system. All activities in the GDS Console are based on roles; when a user logs on to the GDS system, certain roles are assigned to them automatically.
There are three pre-defined roles in the system that should not be edited or removed:
- Everyone: This role is automatically given to every user of the GDS business scenario. It is highly recommended that the Everyone role be assigned to any new user created. Additionally, the Everyone role is essential for basic GDS trade item management, such as Checkout (Edit) and unlock.
- Support: This role provides read-only access for support purposes and has all of the screens but none of the operations assigned.
- Admin: Only users with this role can access the Application Administration menu.
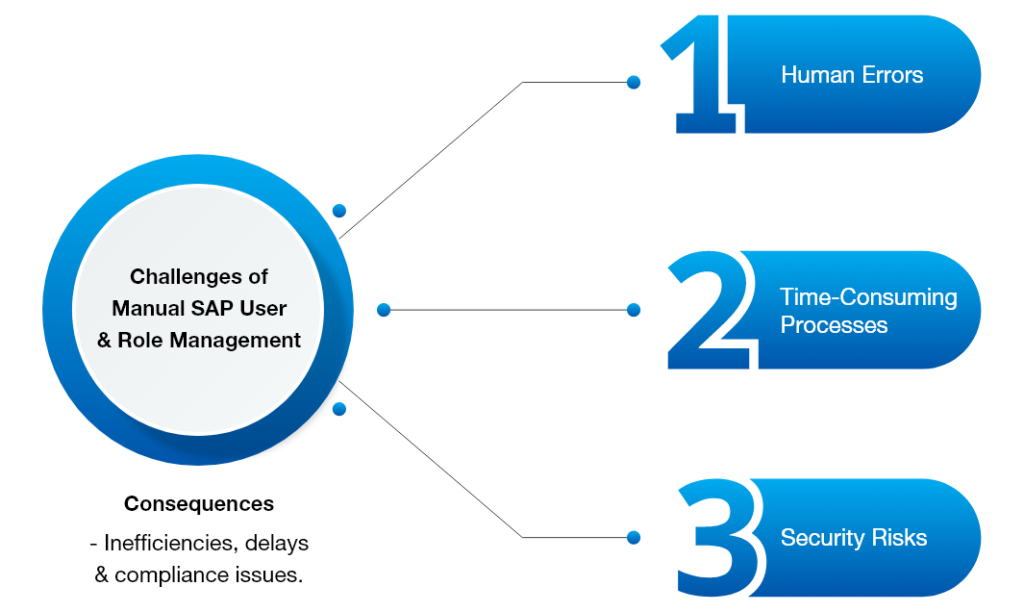
Manual User and Role Management in SAP is associated with certain difficulties, for example, human mistakes, tedious processes, and security threats. These issues can cause ineffectiveness, tardiness, and failure to meet regulations.