
Posted On Jan 01 2024 | 11:49
In the modern interconnected digital world, it is crucial to prioritize the security of sensitive data stored in the cloud. With the increasing frequency and complexity of cyber-attacks, it is essential for organizations to implement robust cloud security measures that offer comprehensive protection against potential threats.
The term “cloud security measures” refers to the strategies and protocols put in place by businesses to safeguard their cloud-based assets, networks, and infrastructure. These measures consist of a combination of technical controls, policies, and best practices that aim to effectively identify, prevent, and respond to security breaches.

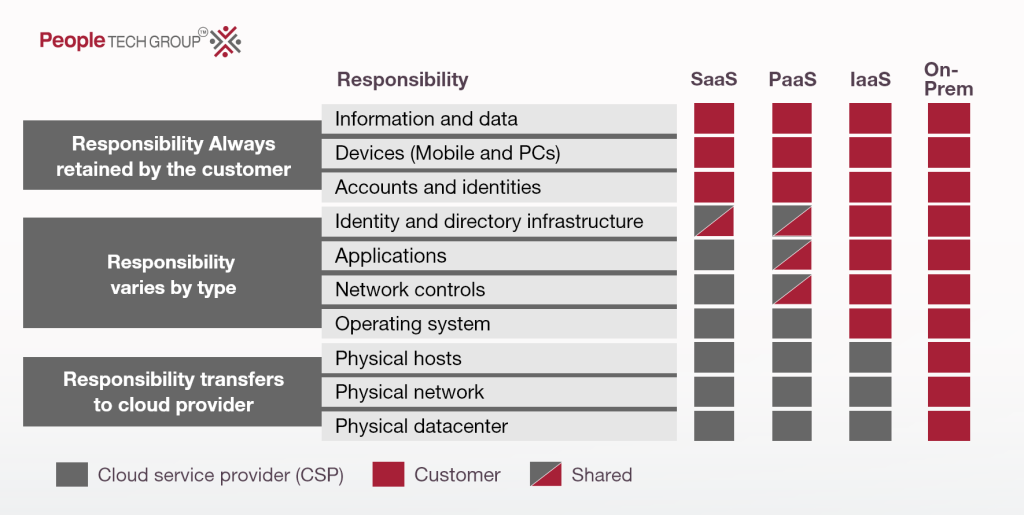
In cloud computing, the shared responsibility model is a commonly used framework to outline the duties of both cloud service providers (CSPs) and customers in ensuring the safety of data, applications, and infrastructure in the cloud. This model helps to establish a clear understanding of each party’s responsibilities in terms of security. While the specific responsibilities may vary among different cloud providers, the overall concept remains consistent.
Here is the shared responsibility in the cloud for cloud service providers and customers:
- CSPs are responsible for the physical security of the data center, servers, network, and storage equipment, and the hypervisor and network security.
- Customers are responsible for securing their data, applications, and configurations and managing identity and access.
- Loss of Control: Some may worry that giving up physical control equates to less security.
- Data Privacy and Compliance: There is a concern that cloud services may not adequately comply with data privacy regulations or industry standards.
- Security Breaches: Having data stored outside of their own premises can be seen as a security risk.
- Vendor Lock-in: Some are worried about being tied to a specific cloud provider due to dependence on their services or proprietary technologies.
- Insider Threats: Deliberate or unintentional actions by employees, contractors, or other insiders can pose a significant threat to cloud security.
- Network Security Challenges: Insufficient network security measures can leave sensitive data vulnerable to interception or unauthorized access.
- Data Loss and Recovery Mechanisms: Data loss can occur due to accidental deletion, system failures, or other unexpected events.
- Emerging Technologies and Threats: As cloud technology advances, new security challenges and threats may arise.
- Misconfiguration and Inadequate Access Controls: The complexity of cloud environments can lead to security vulnerabilities through misconfiguration.
- Understanding the Shared Responsibility Model: Failure to comprehend and implement the shared responsibility model can lead to confusion about security responsibilities.
- Identity and Access Management: Weak IAM practices can result in unauthorized access, privilege escalation, or insider threats.
