
Posted On Mar 03 2024 | 14:19
Have you ever pondered the potential hazards that your company may encounter when sharing data with a third party? It is common for companies to engage in third-party data sharing as part of their regular operations. While this practice offers many advantages, it also comes with potential risks.
A strong plan is necessary to effectively handle these potential risks.
In this blog, you will fully understand data sharing and learn effective strategies to minimize potential risks.
Now, let’s jump right in.
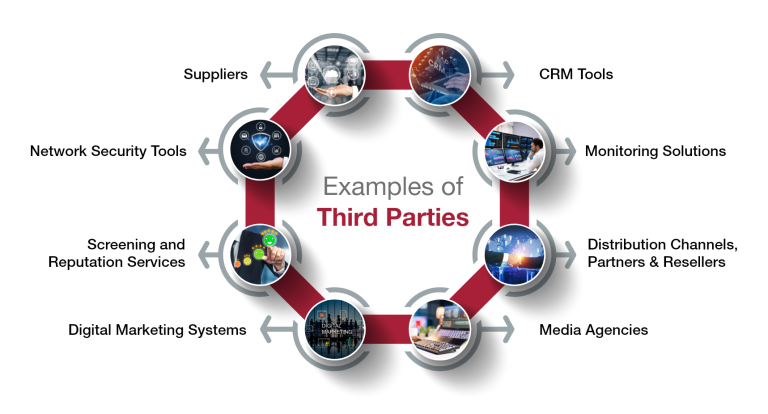
- Suppliers: Supply necessary products or materials to ensure smooth business operations.
- Distribution Channels, Partners, and Resellers: Assist in sales, expand the company's reach, and contribute to generating revenue.
- Network Security Tools: Strengthen the company's cybersecurity measures to protect sensitive data.
- Monitoring Solutions: Offer real-time analytics, improving decision-making and overall efficiency.
- CRM Tools: Streamline customer data management and personalized marketing, leading to better customer retention.
- Digital Marketing Systems: Enhance marketing efforts through automation and tracking, resulting in improved outreach and revenue growth.
- Screening and Reputation Services: Provide support for background checks and reputation management, maintaining a secure business environment.
- Media Agencies: Manage a company's branding, advertising, and public relations, influencing public perception and success.
The sharing of third-party data refers to the practice of acquiring, combining, and exchanging information about individuals, which is usually gathered from different platforms and websites, by entities other than the initial users and collectors of the data. For instance, a Data Management Platform (DMP) might aggregate and share this data.
The process of exchanging information allows companies to obtain diverse and extensive data sets that offer valuable insights into consumer behaviors, habits, and preferences. This practice is widely utilized in targeted advertisements, social media marketing, and predictive analysis.
As intermediaries, DMPs gather considerable amounts of structured and unstructured data from various sources, organize it into manageable segments, and provide access to this data for businesses to use in making informed decisions.
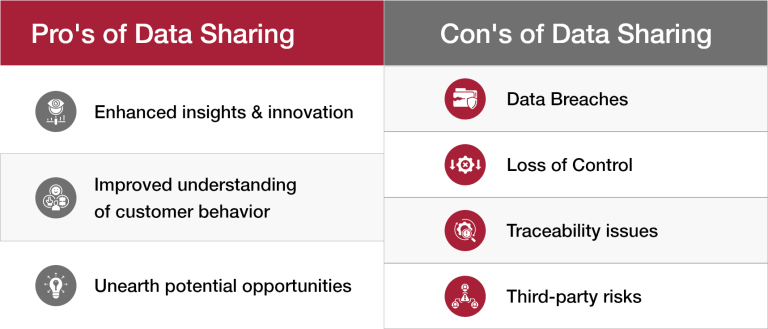
Even though utilizing third-party data has advantages, there are concerns regarding the protection and security of the data. Therefore, companies engaged in third-party data sharing must adhere to data privacy regulations such as GDPR and prioritize the protection of user data.
Third-party risk encompasses the potential dangers posed by third parties, including service providers and vendors, who may have an indirect impact on the stability or security of an organization. This type of risk can be categorized as operational, cyber-security, legal, financial, or reputational in nature.
Data breaches are a major concern when it comes to third-party risk. When a company shares data with outside parties, there is a risk of vulnerabilities if the other entity does not take proper precautions. This could result in the exposure of sensitive data to unauthorized individuals.
One aspect of third-party risk is the potential for rapid response complications. A company’s ability to quickly respond to crises may be hindered by their lack of control over the operations of third-party entities.
Furthermore, companies might face potential hazards when teaming up with external partners who do not have strong data management protocols. This could potentially jeopardize the security of data, compromise its accuracy, or result in its improper use.
The process of managing third-party risks includes the recognition, assessment, and reduction of potential risks that may arise from collaborating with external vendors. This typically entails performing thorough investigations, setting up agreements for data sharing, keeping track of vendor performance, and implementing measures for data privacy and security.
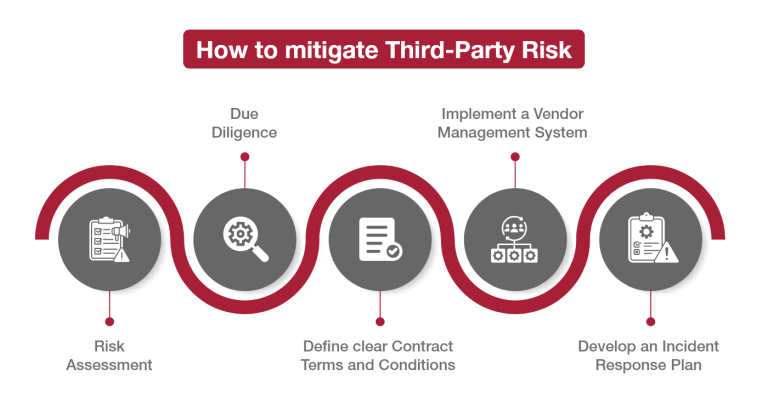
To reduce third-party risk, it is important to have a strong program in place for managing such risks. This program should include:
Now, let’s delve deeper into each of these measures.
1. Evaluation of potential risks
To begin, it is important to perform a thorough evaluation of the potential third-party vendor’s risks. This should include examining all aspects of their business, such as their financial stability, ability to adhere to agree upon terms and conditions, as well as their reputation and past experiences with security incidents.
When considering outsourcing to a third party, it is important to also consider their location and how political or economic instability may affect their business.
2. Conducting thorough research
The implementation of due diligence procedures is crucial in verifying that the third parties you collaborate with have strict safeguards in place, including procedural, technical, and administrative measures. It is important to devote sufficient time to carefully assess their policies, certifications, and service level agreements (SLAs).
Are the certifications relevant to their industry and yours, such as ISO 27001 or SOC 2, possessed by them? Are they performing frequent security audits and providing access to the outcomes? Do their SLA terms match your anticipated standards?
Carefully examine their agreements for any undisclosed obligations or duties.
The full process is automated by
People Tech Group, providing a convenient solution for handling and reducing your third-party risks.
3. Clarify the Terms and Conditions of the Contract
When creating agreements, clearly state your requirements for the third party. This should include your guidelines for data protection, the consequences for failure to comply, and the specific goals they are required to achieve.
The terms of your agreement should also clearly state the regulatory requirements that you are required to adhere to, such as GDPR, CCPA, or HIPAA, and reiterate the third party’s responsibility to adhere to these regulations.
4. Ongoing surveillance
After successfully bringing in a third party, the work does not stop. It is important to constantly monitor their operational performance, compliance with the terms of the contract, and key performance indicators (KPIs).
It is important to regularly perform audits and evaluations to ensure that third-party entities remain compliant and meet your expectations. It is also prudent to be open to modifying your business strategies as the market evolves.
Once more, People Tech has the potential to be a valuable partner, offering effortless surveillance and prompt suggestions for handling potential dangers and hazards.
5: Introduce a System for Managing Vendors
It is important to have a strong vendor management system (VMS) in place to efficiently handle multiple third-party vendors. A reliable VMS enables you to maintain thorough documentation of all third-party partnerships, monitor their effectiveness, and identify any potential hazards.
The development of technology, including
AI and Data Science, has empowered the creation of automated and streamlined systems that can provide continuous risk monitoring and issue notifications when a deviation from the usual pattern occurs.
6. Create a strategy for responding to incidents
If an external entity is responsible for a security breach, it is imperative to have a comprehensive incident response strategy in place. This strategy must outline measures to control and resolve the issue, protocols for informing impacted parties, and adherence to any relevant regulatory requirements.
The use of predetermined communication protocols informs all involved parties of their duties and outlines the necessary procedures for escalation to mitigate the incident’s impact.
Implementing the six steps outlined above can assist in establishing a robust cybersecurity program and mitigating potential risks related to third-party vendors. It is crucial to note that this is a continuous effort, requiring vigilant monitoring of vendor partnerships, ensuring their adherence to current security protocols, and holding them responsible for their compliance.
To effectively share third-party data, it is essential to have a comprehensive and expert solution. This is where People Tech Group (People Tech – Fueling Innovation and Building Beliefs) can assist you. Our range of tools and technologies are designed to ensure the protection and adherence to current security protocols for your data, empowering you to make informed decisions that safeguard your business.
For those looking to expand their knowledge on how People Tech can assist in handling third-party data sharing, schedule a complimentary demonstration by visiting Cyber Security – People Tech Group today.
