Posted On Nov 03 2025 | 16:55 PM
Autonomous Cybersecurity: How AI is Revolutionizing the Future of Digital Defense
Understanding Autonomous Cybersecurity
Autonomous cybersecurity represents the next step in digital defense systems that can detect, analyze, and respond to cyber threats with little to no human intervention. Powered by artificial intelligence and machine learning, these systems continuously learn from data, adapt to new attack patterns, and make real-time security decisions to protect digital environments.
To better understand how cybersecurity has evolved to this stage, the infographic below illustrates the shift from manual and rule-based systems to self-learning, autonomous defenses that operate at machine speed.
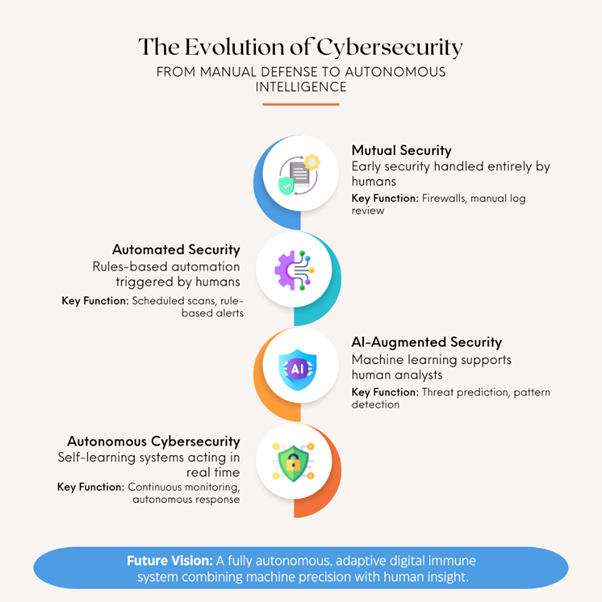
Key Distinction: Autonomous vs Automated Cybersecurity
| Feature | Automated Cybersecurity | Autonomous Cybersecurity |
|---|---|---|
| Decision-making | Follows predefined rules | Learns and makes decisions independently |
| Human involvement | Requires human triggers | Minimal human input |
| Response speed | Reactive | Real-time, adaptive |
| Learning capability | Limited or none | Continuously learns from data |
| Example | Blocking repeated failed logins | Predicting and preventing zero-day attacks |
Core Components
- Machine Learning and Deep Learning: Analyze large datasets to detect patterns and unknown threats like zero-day exploits.
- Behavioral Analytics: Monitor user, device, and application behavior to spot unusual activity.
- Threat Intelligence Integration: Combine data from multiple sources to stay ahead of emerging attacks.
- Autonomous Response Engines: Automatically isolate affected systems, block malicious activity, and remediate threats in real time.
Why Traditional Cybersecurity Is No Longer Enough
The cyber threat landscape has grown too vast and fast for traditional defense methods to keep up. Modern attacks evolve in real time, often leveraging AI and automation, which can outpace human-led security teams.
- High volume and speed of attacks: Zero-day exploits, ransomware, and AI-generated threats are increasing rapidly, overwhelming conventional monitoring systems.
- Human limitations: Cybersecurity skill shortages and delayed manual responses create exploitable gaps.
- Complex infrastructures: Cloud services, IoT devices, and hybrid networks expand attack surfaces, making defense more challenging.
- Example: In recent breaches, attackers moved laterally within networks for weeks before detection - a delay that autonomous systems could have prevented by isolating threats in real time.
How Autonomous Cybersecurity Works
Autonomous cybersecurity functions as a self-learning defense system that protects digital environments with minimal human input. It continuously monitors network traffic, user activity, and endpoints to detect unusual patterns and predict potential attacks using AI and machine learning.
When a threat is identified, the system can automatically isolate affected devices, block malicious actions, and initiate containment measures in real time. Each incident feeds back into the system, improving its accuracy and resilience for future threats. Autonomous tools also integrate with Security Operations Centers (SOCs), enhancing human analysts with real-time insights and faster decision-making.
Key Technologies Powering Autonomous Cyber Defense
| Technology | Primary Function |
|---|---|
| AI & ML | Pattern recognition and predictive defense |
| Behavioral Analytics | Identifying abnormal user behavior |
| NLP | Understanding text-based threat data |
| SOAR | Coordinated response automation |
| Predictive Threat Intelligence | Anticipating new attacks |
Benefits of Autonomous Cybersecurity
- Instant Response: Detects and reacts to threats immediately, reducing the window for attackers to cause damage.
- Scalability: Handles large volumes of data and complex network environments without additional resources.
- Consistent Vigilance: Operates 24/7, eliminating human fatigue and errors.
- Proactive Threat Detection: Identifies potential risks before they impact systems.
- Resource Optimization: Frees cybersecurity professionals from routine monitoring, allowing focus on strategy and advanced threat analysis.
Real-World Applications and Case Studies
Autonomous cybersecurity is already transforming multiple sectors. In enterprise networks, it enables automated malware detection and endpoint protection, reducing response times and limiting damage. Critical infrastructure, such as energy, healthcare, and transportation, increasingly relies on AI-driven defense to protect essential services from sophisticated attacks.
Cloud and hybrid environments benefit from autonomous systems that secure distributed networks and dynamic workloads. Leading companies like Darktrace, Sentinel One, and CrowdStrike Falcon demonstrate practical implementations, using AI to identify threats, respond in real time, and continuously improve detection accuracy. These examples highlight how autonomous cybersecurity enhances resilience across industries.
Challenges and Ethical Considerations
- False positives and overreliance: AI misjudgments can lead to incorrect responses or missed threats.
- Transparency and accountability: Determining who is responsible for autonomous decisions can be difficult.
- Data privacy: Balancing autonomous actions with compliance requirements such as GDPR and CCPA.
- Adversarial AI: Attackers may use AI to deceive or bypass autonomous defenses.
- Human oversight: Maintaining a human-in-the-loop for critical decisions ensures ethical judgment and complements automated systems.
The Future of Autonomous Cybersecurity
Advanced technologies and human-AI collaboration will shape the future of cybersecurity. Trends include integration with generative AI, self-healing networks, and cognitive security agents that can automatically anticipate and neutralize threats. The regulatory landscape is evolving, with new standards and governance frameworks guiding the development of ethical and compliant AI-driven defenses.
Collaboration between humans and AI will form a hybrid model, combining machine speed with human judgment. The ultimate vision is a fully autonomous, adaptive digital immune system capable of defending organizations proactively, learning continuously, and responding to threats faster than ever before.
Conclusion
Cybersecurity is entering a new era, evolving from simple automation to intelligent autonomy. As cyber threats grow faster and more sophisticated, organizations need systems that can learn, adapt, and respond at machine speed. Autonomous cybersecurity enables proactive defense, minimizing risks before they escalate and ensuring resilience in an ever-changing digital landscape.
FAQs
Autonomous cybersecurity uses AI and machine learning to detect, analyze, and respond to cyber threats with minimal human intervention.
Automated systems follow predefined rules, while autonomous systems learn from data and make independent, real-time decisions.
AI/ML, behavioral analytics, NLP, SOAR, and predictive threat intelligence enable continuous monitoring, threat detection, and automated response.
It provides instant response, 24/7 vigilance, proactive threat detection, scalability, and frees cybersecurity teams for strategic tasks.
Potential issues include false positives, ethical concerns, data privacy compliance, adversarial AI, and the need for human oversight.
