
Posted On Aug 08 2024 | 11:57
The modern era has created significant opportunities for businesses, but it has also introduced a relentless threat landscape. Cyberattacks are no longer a matter of “if” but “when,” and traditional security measures are no longer enough. This is where cyber resilience steps in as the cornerstone of safeguarding your digital assets.
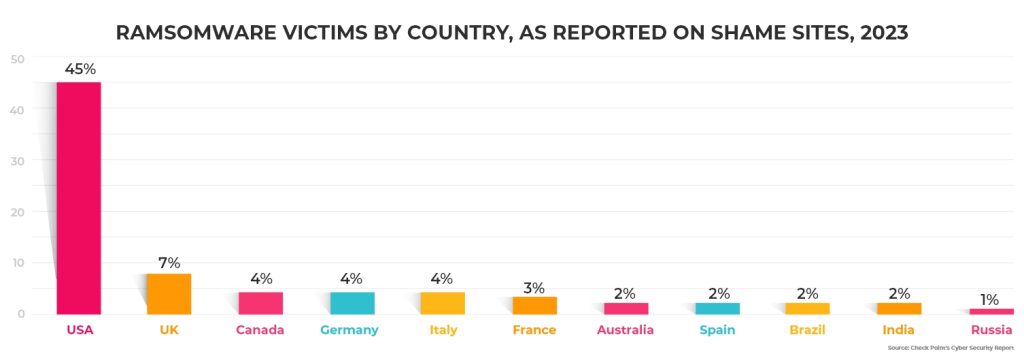
Check Point’s 2024 Cyber Security Report paints a concerning picture: a staggering 90% increase in publicly reported ransomware extortion victims in 2023. This highlights the growing sophistication and prevalence of cyberattacks. Ransomware isn’t the only threat – data breaches, malware attacks, and phishing attempts are just a few examples of the constant barrage businesses face.
Cyber resilience is essential for organizations of every size. Achieving this requires a comprehensive strategy that integrates strong cybersecurity measures, effective incident response, thorough employee training, and strategic planning. By adopting cyber resilience, organizations can endure cyberattacks and continue to prosper in challenging situations.
To learn more about building resilient cloud security, please refer to our two blogs on the topic
Building Resilient Cloud Security – Part 1 & Building Resilient Cloud Security – Part 2
- Maintain core functions during and after cyberattacks, ensuring business continuity.
- Adapt and recover from breaches efficiently, minimizing downtime and financial losses.
- Recognize that every system, no matter how robust, has potential vulnerabilities.
- Fortifying Your Operations: This involves implementing robust security measures to make your environment less susceptible to attacks and minimize the impact if a breach occurs. Here are some key elements:
- Network Segmentation: Dividing your network into smaller segments can limit the spread of a breach if it occurs. By isolating critical systems and data, the damage can be contained more effectively.
- Access Controls: Implementing strong access controls like multi-factor authentication (MFA) restricts unauthorized access to sensitive data and systems. MFA adds an extra layer of security by requiring a second verification factor beyond just a username and password.
- Vulnerability Management: Regularly patching vulnerabilities in software and operating systems is crucial to prevent attackers from exploiting them. Patching should be a prioritized process, with a system in place to identify and deploy updates promptly.
- Data Security: Encrypting sensitive data at rest and in transit adds an extra layer of protection in case of a breach. Encryption scrambles data, making it unreadable to unauthorized users even if it's stolen.
- Security Awareness Training: Educating employees about cyber threats and best practices is vital in preventing social engineering attacks and phishing attempts. Employees are often the first line of defense, and training empowers them to identify suspicious activity and avoid falling victim to cyber scams.
- Incident Detection and Response (IDR): Having a system in place to detect security incidents promptly allows for faster containment and mitigation of damage. Security Information and Event Management (SIEM) solutions can be valuable tools for real-time monitoring and threat detection.
- Incident Response Team: Assemble a dedicated team with clearly defined roles and responsibilities to handle security incidents effectively. This team should include representatives from IT, security, legal, and communications departments. Each member should be trained on their specific role and responsibilities within the incident response process.
- Business Continuity and Disaster Recovery (BCDR) Plans: Having a tested BCDR plan ensures critical operations can resume quickly after a disruption. This plan should outline data backup and recovery procedures, as well as alternative communication channels. Regularly backing up critical data allows for swift restoration in case of a breach.
- Regular Testing and Drills: Regularly testing your incident response plan and conducting security drills helps identify weaknesses and ensure your team is prepared to handle a real-world attack. Drills should simulate different attack scenarios, allowing your team to practice their response and identify areas for improvement.
- Minimized Disruption: A resilient organization can recover quickly from attacks, minimizing downtime and the associated financial losses. The average cost of downtime exceeds a staggering $300,000 per hour. A swift recovery minimizes business disruption and protects your brand reputation. Customers expect uninterrupted service, and cyber resilience helps you maintain their trust.
- Faster Threat Response: Cyber resilience practices improve your organization's ability to detect and contain threats rapidly. This limits the damage caused by an attack and allows you to isolate the breach before it can spread further. The current average time to identify and contain a breach is a concerning 280 days. Faster response times significantly reduce the impact of a cyberattack.
- Reduced Recovery Costs: Tested response plans and backups enable faster data restoration, leading to lower recovery expenses in the aftermath of a cyberattack. Cyber resilience helps you avoid the significant financial burden associated with lengthy data recovery processes and potential regulatory fines.
- Adaptability: A cyber-resilient organization can adapt its security posture by regularly evaluating risks, implementing new controls, and staying informed about emerging threats. This proactive approach keeps you ahead of the curve. By constantly monitoring the threat landscape and adapting your defenses, you can stay one step ahead of attackers.
- Regulatory Compliance: Demonstrating strong cyber resilience practices helps meet regulatory requirements related to cybersecurity risk management, especially for industries like finance and healthcare. A documented cyber resilience strategy provides evidence of due diligence in protecting sensitive data. Compliance with relevant regulations can help avoid hefty fines and penalties.
By prioritizing cyber resilience and implementing a comprehensive strategy with the help of People Tech, Your organization can significantly enhance its ability to withstand, respond to, and recover from cyberattacks. This approach not only protects critical data and assets but also minimizes business disruption, safeguards brand reputation, and fosters trust with customers and partners. Investing in cyber resilience is an investment in the long-term success and sustainability of your business.
Don’t wait for a cyberattack to take action. Begin building your cyber resilience strategy today by conducting a security risk assessment to identify vulnerabilities, developing an incident response plan, and implementing essential security controls.
Wondering how People Tech can take your cyber resilience to the next level?
