
Posted On Feb 02 2024 | 14:11
Have you ever thought about the complex strategies used by cyber attackers to manipulate human psychology and gain access to highly secure systems? Let us explore the world of Social Engineering attacks, where our main goal is to strengthen your organization against the mysterious dangers of Phishing, Vishing, and Smishing. This investigation aims to offer in-depth knowledge on how to protect your business by thoroughly understanding these covert techniques.
- Deceptive Emails: Attackers send emails that seem to originate from authentic entities like banks, government agencies, or reputable companies.
- Spoofed Email Addresses: Phishers may use email addresses that closely resemble legitimate ones to create a false sense of trust.
- Urgency or Threats: Phishing emails often create a sense of urgency, claiming that immediate action is required to address a problem or prevent negative consequences.
- Hyperlinks and Malicious Attachments: Phishing emails hold links and attachments that, when clicked or opened, lead to deceptive websites, or install malicious software on the recipient's device.
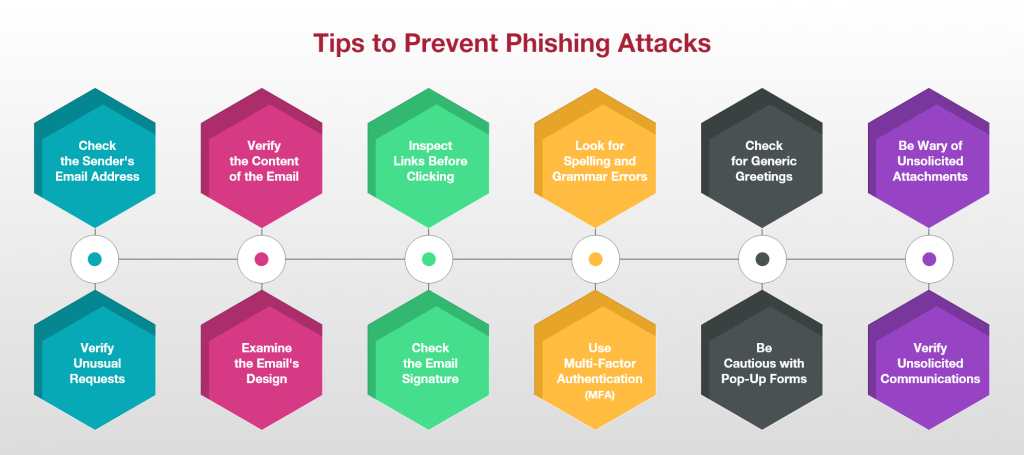
When it comes to businesses, it is crucial to have a strong defense against phishing attempts. This can be accomplished by thoroughly scrutinizing the email address of the sender, as phishers often use variations or misspellings to create fake addresses that look legitimate. It is also important to be cautious of emails that create a sense of urgency, as this is a common tactic used in phishing campaigns. Before clicking on any links, it is recommended to hover over them and check for any suspicious destinations or inconsistent URLs.
Additionally, paying attention to the overall design and professionalism of an email is important, as poorly crafted ones may indicate a phishing attempt. Legitimate emails from reputable sources typically follow consistent and professional design standards, including proper contact information and email signatures. Implementing multi-factor authentication (MFA) is crucial for businesses, as it provides additional security if credentials are compromised.
It is recommended to be cautious when handling pop-up forms in emails, as sensitive information should not be entered into them. Legitimate organizations will direct users to secure websites for such actions. Finally, if you receive unsolicited communications requesting sensitive information, it is important to verify their legitimacy through trusted channels before responding. By following this comprehensive approach, businesses can ensure strong protection against phishing threats that are specifically targeted toward enterprise security.
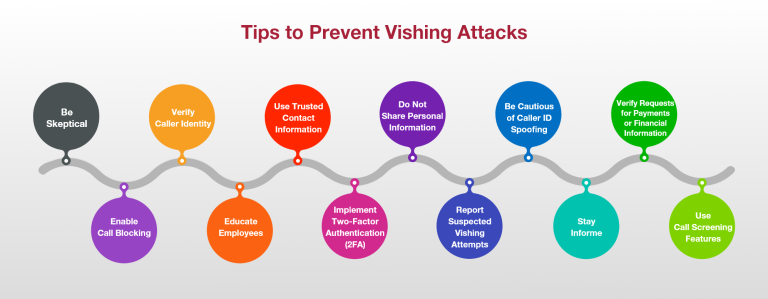
It is important to approach unexpected phone calls with caution, especially when they claim to be from authoritative entities like banks or government agencies. These entities rarely ask for sensitive information over the phone. To verify the caller’s identity, always ask for their name, organization, and call-back number. It is also wise to independently verify this information before sharing any personal details. Exercise caution regarding caller ID spoofing and avoid sharing personal or financial information unless you initiated the call and verified the recipient’s identity.
For added protection, consider using call-blocking tools and call screening features on your smartphone. In a business setting, make sure to educate employees about the risks of vishing, establish protocols for verifying caller identities, and implement two-factor authentication for better security. If you encounter any suspected vishing attempts, report them promptly to your organization’s IT or security team. Stay updated on common vishing tactics to prevent falling prey to constantly evolving social engineering techniques.

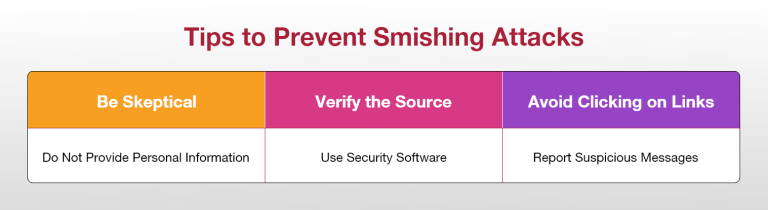
Stay cautious about unexpected texts, especially if they seem urgent or fishy. Before clicking on any links or replying, make sure the sender is legit by checking their official contact info. Be careful with links in messages – only click if you are sure they are safe. Do not share personal info in response to unsolicited texts; real organizations usually do not ask for sensitive details that way. Protect your phone with security software and keep it updated to spot and stop smishing attempts. If you get a weird text, report it to your mobile carrier and the right authorities. Following these steps helps you avoid smishing attacks and keeps your personal info safe.
In conclusion, to prevent Social Engineering attacks, a comprehensive strategy must be employed. This involves increasing awareness, offering educational resources, and implementing robust security protocols. People Tech is dedicated to assisting in the integration of effective strategies and approaches to decrease vulnerability to phishing. This involves taking appropriate measures and offering ongoing assistance for vigilant surveillance and protection. It is essential to recognize that there is no single solution that can guarantee complete protection against phishing risks; therefore, we promote a holistic approach that utilizes technology, education, and user awareness to greatly reduce the chances of becoming a victim of social engineering attacks. Furthermore, People Tech offers services such as Cyber Awareness Training, conducting regular assessments for employees, and monitoring the system for potential data breaches.
