
Posted On Feb 02 2024 | 11:12
Cyber threats looming like wolves at the door for businesses of all sizes. While large corporations might have dedicated security battalions, small businesses often wear the Cybersecurity hat alongside countless others. This often leaves them particularly vulnerable to attacks that can cripple their operations, finances, and reputation.
Why Prioritize Cybersecurity?
- 43% of cyberattacks target small businesses. (Source: Verizon Data Breach Investigations Report 2023)
- The average cost of a data breach for a small business is $4.24 million. (Source: Ponemon Institute, The Cost of Ransomware Report 2023)
- 88% of small businesses don't have a formal cybersecurity incident response plan. (Source: National Cyber Security Alliance 2023 Cybersecurity Awareness Month US Small Business Survey)
These statistics paint a stark picture, but fear not, intrepid entrepreneur! This blog post serves as your battle plan, outlining a practical cybersecurity strategy based on recognized frameworks and essential practices. With the right tools and knowledge, you can transform your small business into a cybersecurity fortress.
Why Prioritize Cybersecurity?
Think of cybersecurity as your business armor. It shields you from:
- Data breaches: Hackers stealing sensitive customer information, financial records, or intellectual property.
- Ransomware attacks: Criminals locking you out of your own systems and demanding exorbitant ransoms to regain access.
- Phishing scams: Deceptive emails or websites tricking employees into revealing sensitive information.
- Operational disruptions: System outages caused by malware or denial-of-service attacks, hindering your ability to serve customers.
- Reputational damage: News of a cyberattack can erode customer trust and damage your brand image.
By investing in cybersecurity, you’re not just protecting your data, you’re safeguarding your business’s very foundation.
Cybersecurity Frameworks: Your Guiding Light
Navigating the complex world of cybersecurity can feel overwhelming. Thankfully, frameworks like the National Institute of Standards and Technology (NIST) Cybersecurity Framework and the Cyber Essentials framework provide structured approaches to managing cyber risk.
These frameworks outline five key steps:
- Identify: Understand your assets, data, and vulnerabilities. Think of this as taking inventory of your castle's valuables and hidden weaknesses.
- Protect: Implement safeguards like firewalls, antivirus software, and access controls. Imagine building sturdy walls, guard towers, and secure gates around your castle
- Detect: Monitor your systems for suspicious activity. This is like having vigilant lookout guards scanning for approaching threats.
- Respond: Have a plan in place to contain and mitigate incidents. Think of this as having a well-rehearsed emergency response plan to repel attackers and minimize damage.
- Recover: Restore impacted systems and data quickly and securely. This is like rebuilding your castle's defenses after an attack, stronger than before.
These frameworks serve as a roadmap, helping you prioritize your efforts and allocate resources effectively.
Engaging with Third Parties: Trust but Verify
In today’s interconnected world, third-party vendors often have access to your data and systems. It’s crucial to assess their security posture through:
- Vendor assessments: Evaluate their security controls and data handling practices. Think of this as checking the credentials and training of your hired guards.
- Regular audits: Verify if they maintain their security standards over time. Regular inspections ensure your guards remain vigilant.
- Collaboration: Work together to address identified vulnerabilities and improve overall security. Imagine your guards and yours working together to strengthen the castle's defenses.
Essential Cybersecurity Strategies:
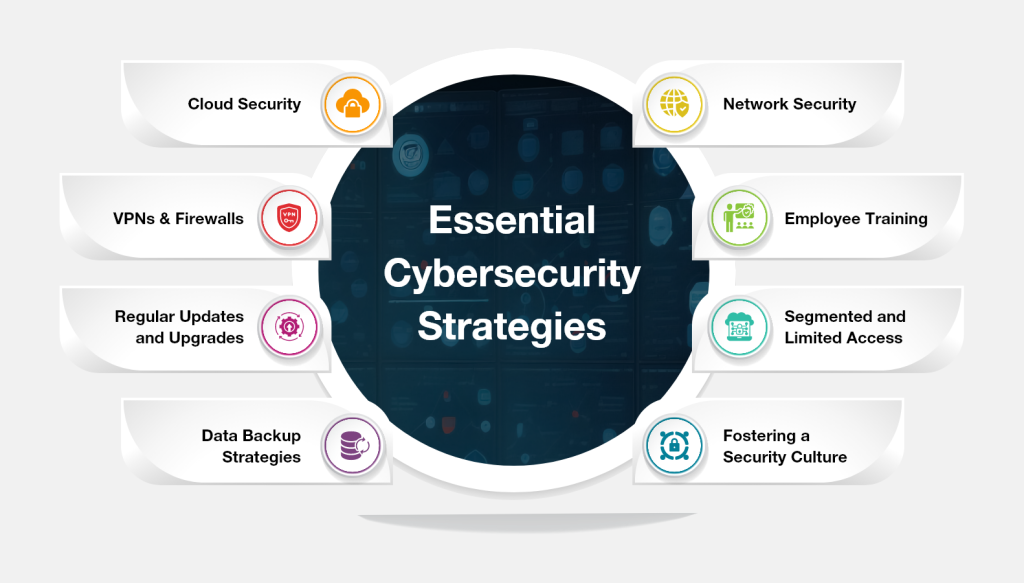
- Cloud Security: Choose reputable cloud providers with robust security features. Imagine partnering with a well-guarded and secure kingdom for cloud storage.
- Network Security: Secure your network with firewalls and intrusion detection systems (IDS). This is like having advanced alarm systems and watchtowers at your network gateways.
- VPNs and Firewalls: Use VPNs for secure remote access and firewalls to filter incoming and outgoing traffic. Think of VPNs as secret tunnels for remote access and firewalls as gatekeepers filtering who enters and exits your network castle.
- Regular Updates and Upgrades: Apply updates to software and operating systems promptly to patch vulnerabilities. This is like regularly repairing and reinforcing your castle walls to address weaknesses.
- Data Backup Strategies: Regularly back up your data and store copies offsite for safe recovery. Imagine having a secure backup vault outside the castle walls in case of attack.
- Segmented and Limited Access: Limit user access to data and systems based on their needs. Imagine assigning access keys and permissions only to those who need them within the castle.
- Employee Training: Educate your employees on cyber threats and best practices to avoid phishing scams and social engineering attacks. Think of this as training your castle guards to recognize and resist deception tactics.
- Fostering a Security Culture: Make security everyone's responsibility by promoting awareness and encouraging employees to report suspicious activity. Imagine your entire castle community being vigilant and reporting any suspicious activity they see.
