
Posted On Jan 01 2024 | 12:48
In our previous part 1 blog, we delved into the concept of the shared responsibility model, as well as the associated risks and threats. Now, in the second part, we will explore the recommended approaches for securing the cloud, including tools, technologies, and effective strategies.
Best Practices for Securing Cloud Environments:
Securing cloud environments requires a multi-layered approach that combines technical controls, policies, and employee awareness. Adhere to the guidelines of the Best Practices Framework for Cloud Security, as outlined by CSA (Cloud Security Alliance) and NIST (National Institute of Standards and Technology).
1. Employ a defense-in-depth approach, using multiple security measures to safeguard organizational assets against cyber threats.
2. Familiarize with the Shared Responsibility Model, implement robust Identity, and Access Management.
3. Encrypt data at rest and during transit; ensure proper security configuration and management.
4. Regularly monitor and audit activities, establish data backups, and implement disaster recovery protocols.
5. Consider compliance and regulatory requirements; create an Incident Response plan.
6. Provide training, increase awareness among employees, conduct vendor assessments, and perform due diligence.
7. Strengthen network security, paying attention to Container and Serverless Security.
8. Conduct periodic external and internal Vulnerability Assessment and Penetration Testing, use Threat Intelligence, Data Loss Prevention measures, and implement Zero-trust security.
In addition to adhering to best practices for securing cloud environments, it is crucial to understand the significance of assessing and evaluating the security of the cloud, including key factors that impact its security posture. Please refer to the accompanying image for a clearer understanding.
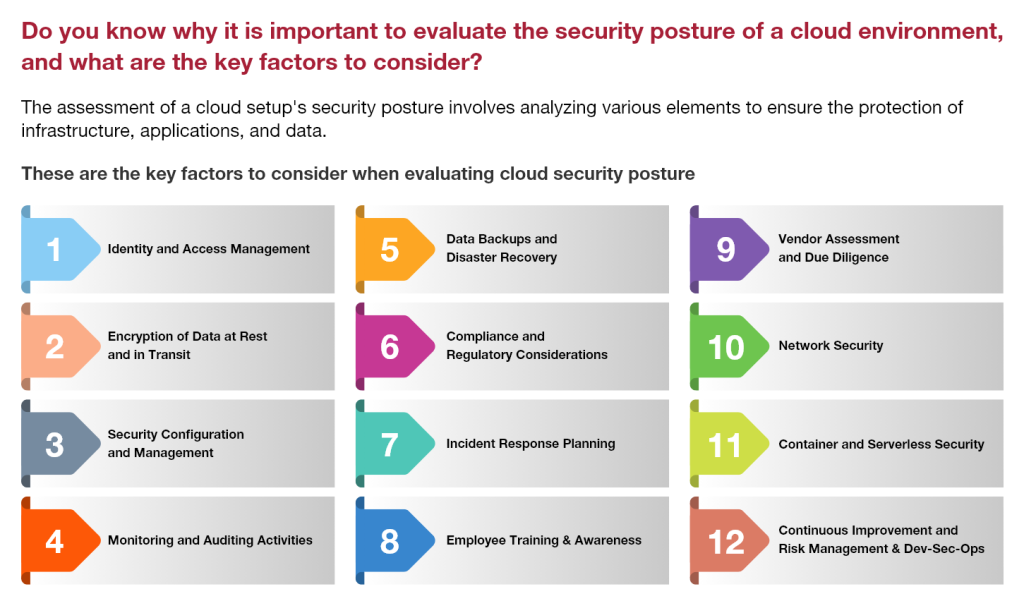
Note: Regularly evaluating and assessing these components assists organizations in identifying potential security vulnerabilities, prioritizing corrective actions, and improving the overall security posture of their cloud environment.
Fig 3 – Shows the importance of evaluating the security posture of a cloud environment and highlights key factors in a concise manner.
Keeping a cloud environment safe requires the utilization of a variety of tools and technologies that can monitor, regulate access, encrypt data, and defend against cyber threats. Each cloud provider offers their own native tools and mechanisms to ensure security within their environment.
Below are some examples of domains and associated Cloud Security Tools and Technologies:
Identity and Access Management (IAM)
- Azure Active Directory (Azure AD): Manages and authenticates users and devices.
Cloud Security Posture Management (CSPM)
- AWS Config and AWS Security Hub: Assess, audit, and evaluate AWS resource configurations.
- Azure Security Center: Provides continuous security monitoring and threat detection for Azure resources.
Vulnerability Scanning and Management
- Nessus: Widely used for vulnerability scanning and management.
- Qualys Cloud Platform: Offers vulnerability management and policy compliance solutions.
Security Information and Event Management (SIEM)
- Splunk: Collects, indexes, and analyzes log and machine data across cloud services.
- Azure Sentinel: Cloud-native SIEM and SOAR (Security Orchestration, Automation, and Response) solution.
Intrusion Detection and Prevention Systems (IDPS)
- Snort: Open-source IDPS.
- AWS Guard Duty: Intelligent threat detection service for AWS environments.
Web Application Firewall (WAF)
- AWS WAF and AWS Firewall Manager: Protects web applications from common exploits.
Encryption and Key Management
- AWS Key Management Service (KMS): Manages encryption keys for AWS services.
- Azure Key Vault: Safeguards and controls access to encryption keys, secrets, and certificates.
Solutions for Limited privacy protections:
- Technologies like anonymization and pseudonymization are excellent privacy-enhancing solutions. Anonymization is the process of removing personal identifiers from data, and pseudonymization replaces the identifiers with pseudonyms to make it harder to identify individuals.
- Furthermore, transparent and clear privacy policies should be in place to make users aware of how their data is collected, stored, and used. It also allows users to opt out or delete their data if they choose to. Security checks and software updates should also be conducted to ensure any privacy vulnerabilities are addressed.
Cloud Access Security Broker (CASB)
- Netskope: Offers visibility and control over data in the cloud.
- McAfee MVISION Cloud: Provides CASB solutions for cloud security.
Container Security
- Docker Security Scanning: Scans Docker images for vulnerabilities.
- Aqua Security: Focuses on container security across the entire lifecycle.
Serverless Security
- PureSec: Specialized in serverless security.
- AWS Lambda Layers for Security Libraries: Incorporates security libraries into serverless functions.
Incident Response and Forensics
- Carbon Black Cloud: Endpoint protection and threat hunting platform.
- CrowdStrike Falcon: Cloud-native endpoint protection.
Data Loss Prevention (DLP)
- Symantec DLP: Comprehensive data protection solution.
- Microsoft Azure Information Protection: Classifies and protects data in Azure.
Continuous Monitoring and Compliance
- CloudTrail (AWS) and Azure Activity Log: Records API calls, providing visibility into actions taken.
- Prisma Cloud (formerly RedLock): Continuous monitoring and compliance for multi-cloud environments.
Mobile Device Management (MDM)
- MobileIron: Offers mobile security and management solutions.
- Microsoft Intune: Provides mobile device and application management.
In addition to tools and technologies, establishing a robust cloud strategy is crucial for safeguarding your organization’s data and infrastructure. For a clearer comprehension of the cloud security strategy, please refer to the accompanying image.
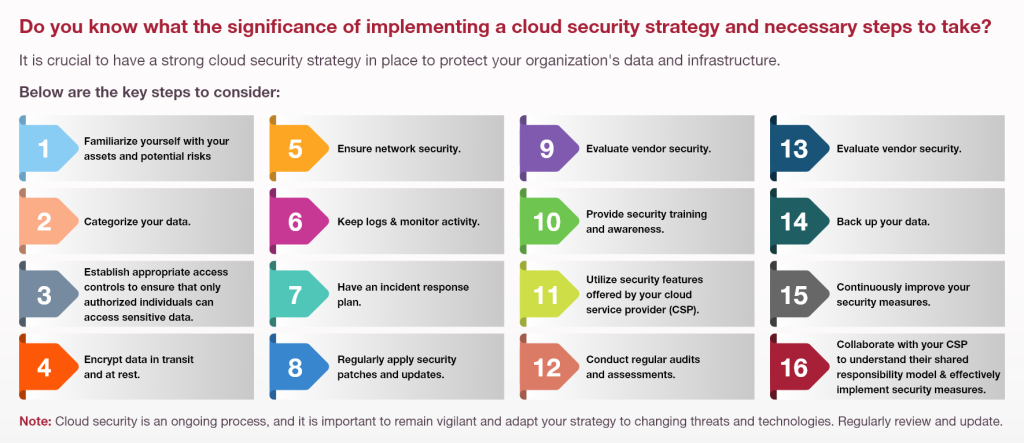
Fig 4 – shows the importance of implementing a cloud security strategy and outlines the necessary steps to be taken.
In the rapidly evolving field of cybersecurity, ongoing developments in trends and technologies are consistently introduced to counteract emerging threats. To stay up to date in this fast-paced industry, it is important to check for industry updates and attend relevant conferences regularly.
Some of the current Cloud security trends and emerging technologies include:
1. Zero Trust Security: It focuses on strict access controls and continuous verification.
2. Artificial Intelligence (AI) and Machine Learning (ML): These are being used for threat detection and anomaly detection.
3. Extended Detection and Response (XDR): Which integrates various security solutions for more comprehensive threat detection and response capabilities.
4. Cloud Security Posture Management (CSPM): These tools are also becoming more popular in ensuring the secure configuration of cloud environments.
5. Identity and Access Management (IAM): It is another important aspect of cloud security, with features such as multi-factor authentication (MFA), biometrics, and adaptive authentication for enhanced security.
6. Container security and edge security: These are also crucial for protecting containerized environments and IoT (Internet of Things) devices and edge computing infrastructure, respectively. In addition, threat intelligence sharing among organizations is becoming increasingly important for identifying and responding to emerging threats.
7. DevSecOps: It involves integrating security into the development pipeline.
8. 5G security: As technology advances, security measures must also adapt, as seen with the need for 5G security measures to address the unique characteristics of this technology.
Conclusion:
In conclusion, building resilient cloud security is crucial for organizations looking to unlock their cloud confidence. We at People Tech Group offer a range of cybersecurity services.
