
Posted On May 05 2024 | 15:31
Did you know that cyberattacks often start by targeting Internet of Things (IoT) endpoints? From there, they sneak across corporate networks to hijack identities and infrastructure. Corporate-owned IoT devices are the top targets, with personal IoT gadgets not far behind.

Security wasn’t a primary consideration in the design of IoT devices, and their growing number and diversity increase the risk of cyber threats. You can’t install security software on most IoT devices, and some may even come with pre-installed malware. That’s why securing the network itself is crucial to protecting your IoT ecosystem.
To learn more about IoT security challenges and understand how to build reliable solutions, check out our detailed blog. IoT Security Challenges and Building Solutions: Part –1 & IoT Security Challenges and Building Solutions: Part -2
- Weak Authentication and Authorization: Many IoT devices use default passwords, making it easy for hackers to access them. Rogue devices on the network can also be used for malicious activities.
- Lack of Encryption: Most IoT device traffic is unencrypted, exposing sensitive data to malware attacks like ransomware. This includes devices used in medical imaging, patient monitoring, security cameras, and printers.
- Vulnerabilities in Firmware and Software: Short development cycles and low budgets for secure firmware leave IoT devices open to basic attacks. Vulnerabilities in standard components affect millions of devices.
- Insecure Communications Protocols: IoT devices often share networks with other devices, allowing attacks to spread. Insecure protocols like HTTP and API can be exploited by cybercriminals.
- Difficulty in Patching and Updating: IoT devices are often not designed for regular security updates, making them vulnerable. Organizations need to implement additional measures to ensure the security of their IoT devices and networks.
The IoT is experiencing rapid expansion, with projections estimating over 19 billion connected devices by 2025. This surge in connected devices offers numerous benefits in terms of efficiency and connectivity but also presents significant security challenges.
Many IoT devices prioritize convenience and functionality at the expense of robust security, making them appealing targets for cyber attackers. These weaknesses can result in unauthorized access, data theft, and the use of devices in larger botnet attacks.
- a. Manufacturer Responsibility: Manufacturers must integrate security measures from the development phase, including strong encryption, secure authentication protocols, and regular firmware updates.
- b. Organizational Measures: Organizations deploying IoT solutions should regularly assess and monitor device security, implement network segmentation to limit breach impacts, and use advanced security solutions like intrusion detection systems designed for IoT.
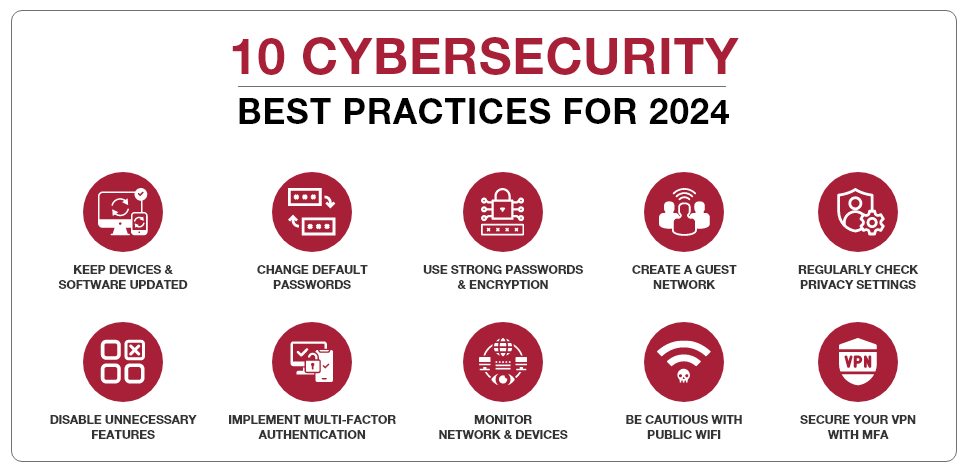
- Keep Devices and Software Updated: Regularly update all IoT devices with the latest firmware and software to patch vulnerabilities and enhance security.
- Change Default Passwords: Replace default passwords with strong, unique ones to prevent unauthorized access.
- Use Strong Passwords and Encryption: Implement complex passwords and robust encryption methods like WPA2 for WiFi networks to protect communications. Consider securing your WiFi network with Multi-Factor Authentication (MFA).
- Create a Guest Network: Establish a distinct guest network on your router to isolate potentially compromised devices brought by visitors from your main network.
- Regularly Check Privacy Settings: Review and adjust the privacy and security settings of your IoT devices to ensure they meet your requirements.
- Disable Unnecessary Features: Turn off any unused features on your IoT devices to reduce potential vulnerabilities.
- Implement Multi-Factor Authentication: Utilize MFA wherever possible to enhance security beyond just passwords.
- Monitor Network and Devices: Monitor all devices connected to your network for any unusual activity that might signal a security breach.
- Be Cautious with Public Wi-Fi: Remotely manage IoT devices, utilize a Virtual Private Network (VPN), especially on public Wi-Fi networks.
- Secure Your VPN with MFA: Ensure that your VPN is secure with MFA to protect remote access as much as on-site access.
In conclusion, the future of IoT security hinges on a collaborative effort. Manufacturers must prioritize built-in security, organizations need robust practices, and advancements in AI offer promising solutions for threat detection. By adopting the a forementioned best practices, you can significantly improve your IoT security posture.
Remember, vigilance is key. Stay updated on the latest threats and don’t hesitate to seek expert guidance. People Tech Group is here to help you navigate the ever-evolving IoT landscape and ensure your connected devices remain secure with our best cybersecurity services.
Contact us today and unlock a future of worry-free connectivity!
