Posted On May 09 2023 | 12:04
Think You Know Secure Coding? These 10 Expert Tips Might Surprise You
Did you know that over 90% of software vulnerabilities are caused by simple coding mistakes?
Indeed, most breaches don’t start with a high-tech hacker attack. They begin with a small flaw in the code that someone forgot to secure. That’s where secure coding comes in. It’s the practice of writing software in a way that prevents vulnerabilities from ever entering your codebase. From input validation and API security to error handling and secret management, secure coding isn’t just a checklist—it’s a mindset that today’s best tech teams live by. But here’s the kicker: even experienced developers often miss the mark.
This blog isn’t about generic advice. These are 10 expert-approved secure coding tips used by top-performing teams around the world, and a few might just surprise you.
Let’s dive in.
Expert Tips for Secure Coding
1. Shift Left—Start Security Early
Waiting until the testing phase to think about security is like locking the door after the intruder is inside. Top tech teams “shift left,” integrating security from the earliest stages of the development lifecycle—planning, architecture, and design. They involve security experts during requirements gathering, use threat modeling before coding starts, and build secure patterns into their frameworks from day one. This proactive approach reduces the cost of fixing vulnerabilities later and prevents insecure code from ever being written.
2. Sanitize All User Inputs
User input is a hacker’s playground if not handled correctly. Whether it’s form fields, URLs, or API requests—everything must be validated and sanitized. Failing to do so opens the door to injection attacks like SQL injection, command injection, and cross-site scripting (XSS)—all listed in the OWASP Top 10. Always assume user input is malicious until proven otherwise and use allowlists, type checking, and proper escaping as standard practices.
3. Avoid Hard-Coding Secrets
It might seem convenient to store API keys, tokens, or credentials directly in your code, but it’s also a massive security risk. If your repo ever gets leaked—even by mistake—those secrets are exposed. Instead, use environment variables or secret management tools like Hashi Corp Vault, AWS Secrets Manager, or Azure Key Vault to store sensitive data securely. It’s one of the simplest changes with one of the biggest impacts.
4. Use Parameterized Queries
SQL injection attacks can grant unauthorized access to your database with just a few keystrokes—unless you’re using parameterized queries. Instead of concatenating strings directly in SQL statements, use placeholders that bind values safely. Most modern programming languages and ORM tools (like Python’s SQLAlchemy or Java’s Prepared Statement) support this out of the box. This small shift neutralizes malicious input and keeps your data safe.
5. Implement Proper Authentication & Authorization
Don’t just ask who’s logging in—ask what they’re allowed to do. Authentication verifies identity; authorization determines access. Use strong, modern authentication methods like OAuth 2.0, JWTs, and multi-factor authentication (MFA). Combine that with strict role-based access control (RBAC) or attribute-based access control (ABAC) and follow the principle of least privilege: users should only have access to what they absolutely need.
6. Secure APIs Like They’re Public
Even private APIs can be exposed unintentionally, so treat all APIs as if they’re open to the world. Secure them with authentication tokens, rate limiting, and input validation. Use tools like Postman Security, Swagger with security definitions, and API gateways that enforce policies and monitor traffic. Top teams monitor API abuse patterns and always encrypt data in transit using HTTPS/TLS.
7. Keep Dependencies Updated
Your application might be secure, but are the libraries it depends on? Outdated third-party components are one of the most common entry points for attackers. Use Software Composition Analysis (SCA) tools like Snyk, WhiteSource, or Dependabot to regularly audit dependencies and get alerts about known vulnerabilities. Automate updates wherever possible to avoid falling behind.
8. Secure Coding Across the DevOps Lifecycle
Secure coding isn’t just about writing better functions it’s about embedding security throughout the entire DevOps pipeline. From initial development to production deployment, each phase is a potential vulnerability point if not handled securely.
The image below illustrates how developers and DevOps admins interact with a wide array of tools across the lifecycle:
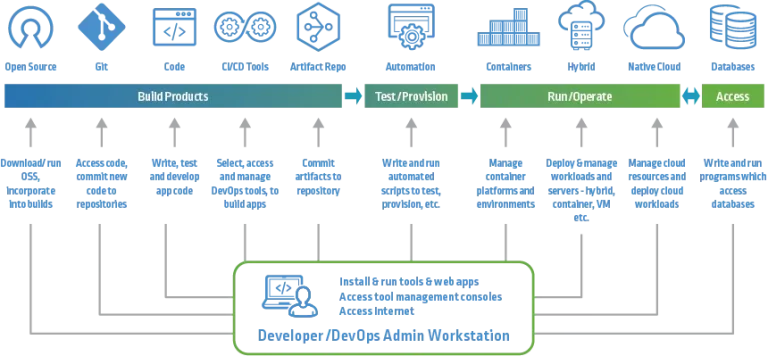
- Build Phase: Developers download open-source software (OSS), commit code via Git, write and test application logic, manage CI/CD pipelines, and push artifacts to repositories.
- Test/Provision: Teams use automation tools to run security scans, provisioning scripts, and validate configurations.
- Run/Operate: This is where workloads are deployed and managed across hybrid, containerized, or cloud-native environments.
- Access: Applications and services interact with databases and external systems—this is where secure access control and data protection are critical.
Each touchpoint from source code to deployment is an opportunity to “bake in” security, not bolt it on later.
9. Handle Errors Gracefully
An error message should never be a blueprint for your attacker. Stack traces, debug info, or even verbose API responses can leak critical details about your environment or code structure. Log errors securely on the backend, show only generic messages to users, and never reveal implementation details. Tools like Sentry or ELK Stack can help you manage logs without compromising security.
10. Educate Your Developers Continuously
Security isn’t a one-time training—it’s a culture. Elite teams invest in ongoing developer education through secure coding workshops, internal wikis, code reviews, and even gamified platforms like Secure Code Warrior or Hack the Box. Regular exposure to real-world vulnerabilities and secure coding patterns helps developers think like attackers and code like defenders.
Think You’re Covered? Think Again.
Even the most experienced developers can overlook the basics when it comes to secure coding. That’s because security isn’t always flashy but it’s essential. The truth is that most vulnerabilities come from small, preventable mistakes that slip through the cracks when speed is prioritized over safety.
Remember: security isn’t a one-time checklist. It’s a continuous mindset. The best tech teams know this, and they embed secure practices into every stage of development from planning to production.
So, here’s your challenge: take a moment to audit your current workflow. Are you sanitizing inputs? Are secrets hard coded? Are your dependencies up to date? Start by picking just 2–3 tips from this list and putting them into practice. It could be the difference between a safe product and the next breach headline.
